Welcome back! Football's second week did not disappoint at all...my Eagles found another way to win despite an anemic offense, the Bengals lost a heartbreaker at home, the 49ers are starting to look unstoppable, and the Giants, Steelers, and Chiefs all proved that fortunes could change on any given Sunday. Another really exciting week with some real 4th quarter nail biters!
I love football...
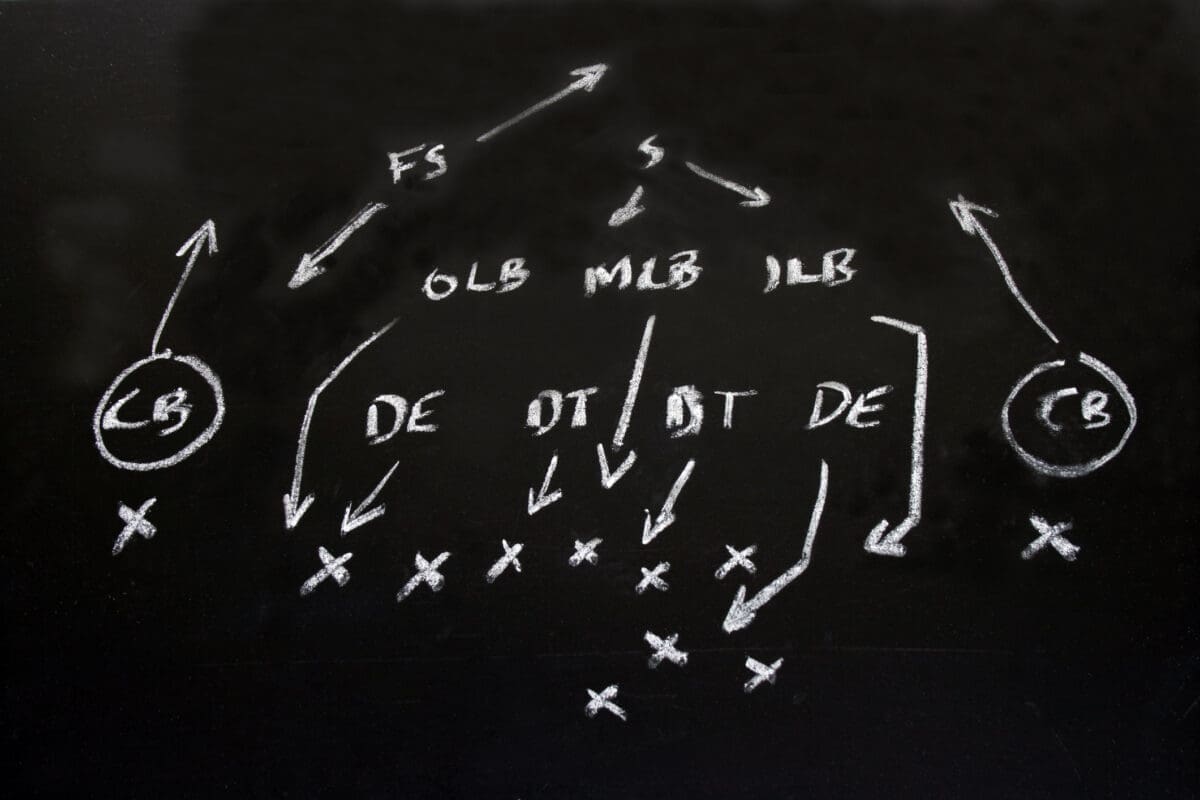
Games this week were won and lost by defense so let's talk about defense and the people you need on your defensive roster to be successful as a security leader.
Defense
The defensive phase itself in football has 3 sections - coverage, interior, and line. These are handled by defensive backs (corner/safety), linebackers (outside and inside), and defensive linemen (defensive tackles and ends) respectively. This kind of alignment is the equivalent of Defense-In-Depth strategies in cyber security.
The coverage section is there to minimize and localize penetration that can put the opposition in the end zone; the "bend don't break" strategy. In cyber security this would be the same as prevention. Your prevention strategy should be focused on making vertical movement through your infrastructure impossible, and ensuring lateral movement is identified and contained.
The interior section is there to limit the opposition's ability to move beyond containment zones as well as recognize when there's a problem that could become an incident. This is similar to security's response phase - this is where we make sure we are able to block and tackle events that occur and limit both lateral movement and
The line represents the detection phase for security. We want to prevent the opponent's ability to make significant gains and frustrate our opponent into making critical mistakes. We know our opponents will move the ball, but we want to minimize and localize movement as much as possible. In football, if you can only move the ball 6 yards in 3 tries, you have to punt to the other side because you only get 4 tries to move 10 yards. The line represents the 1st line of defense, so let's start there.
Detection
This is an area that could be outsourced, but still requires oversight to be effective. So, what I'm saying here is DON'T RELY ON VENDORS ALONE! You should have a resource or two who can provide oversight of your vendor's detection mechanisms, anomalies, and actions, and ensure there is clear and consistent communication between your organization and there. Your vendor should see their SOC offering as a 3-tiered approach aligned to a security framework you've already integrated. This ensures long-term alignment and can reduce false positives and timewasters. A vendor that is not gung-ho about routine huddles with your team on detection events and high-level trends is probably not a vendor you want to work with.
If you do have your detection resources in-house, you should have someone who is responsible for event management - usually your SOC (security operations center). A lot of people will debate me around the roles you need in a SOC but I'm a KISS (keep it simple and stupid) method type of guy, so I look at security roles in that same way. The roles you'll need in a SOC will depend on the risks that need to be covered in your organization. If you make products, you'll need AppSec and coders with a security background in your SOC. If you house consumer data, you'll need data specialists in your SOC. Regardless of those nuances, you'll always need analysts who examine tickets and correlate information and engineers who can either propose changes to your tech stack or make changes themselves following your organization's change control mechanisms. The latter aspect will vary greatly depending on where security sits in your organization and who is accountable for technology delivery.
How many people you need in-house depends on your assessed operational risk (special teams helps you figure this one out), and as a leader you should articulate the investment in personnel based on that assessed operational risk and appetite. If you're a 24x7x365 business, you should have a SOC that is positioned accordingly. Most companies take the hybrid approach to contain payroll costs - a sunset to sunrise SOC that is out-sourced with a single-shift interior SOC.
SOCs in larger organizations are typically broken into tiers, with your 1st line providing triage of events, 2nd line providing correlation and analysis, and the 3rd line providing remediation/mitigation advice and/or diving deeper to understand scope and provide control factors to other departments outside of security and IT.
I used to employ a sunset to sunrise SOC that contained tier 1 and 2 personnel with my tier 3 people doing roving on-call (but they never got a call afterhours). Then during the day our outsourced SOC just handled tier 1, while my 2 and 3 people handled verified tickets. It was cost-effective and efficient because we had a good vendor...selecting the right partner is key here.
Response
Cyber security response can be outsourced, especially incident response. In my view, one of the most critical things you can build for your security organization is a strong discipline around incident management and playbooks. Similar to the detection phase, you need people in-house who can manage your response vendors. An outsourced vendor will rely on your organization to ensure they're looking at the right things, building the right playbooks, designing the right response strategies to fit your individual business. Hopefully you're seeing a trend here - nothing about cyber security allows you to just hand-off responsibility.
In-house your response personnel should be tuned to scenario testing, forensics, classification & analysis, and incident response (which should include validation). Your containment personnel might be found here as well.
You could do all of this with the right 2 or 3 people on your team who work as a team rather than siloed efforts. The key here is ensuring the response chain is respected throughout. Information that comes in from the SOC should be further scrutinized against the baseline to understand what's happening. The tickets that analysts in the SOC work on should be validated and classified for further use should an alert condition be repeated. The other advantage here is having two sets of eyes on the same data but from different perspectives. The SOC looks at the whole forest, the response teams examine the trees.
Playbooks are developed at the response phase. Playbooks are essential to ensuring technical teams AND business units know what to do when something goes wrong. Where your response team develops the processes and procedures around playbooks, your special teams align them with the organization, and your offensive teams help vet the scenarios. Again - this is a team effort requiring all phases to work together.
SIDEBAR: The recent events surrounding MGM (who manage my favorite properties in Vegas btw) should be a reminder to all of us the importance of developing strong playbooks, continuous testing, and routing tabletop exercises to expose weaknesses. We have to keep in front of us that attacks are not a matter of IF but WHEN and it's our fiduciary responsibility to plan for failure and design for resilience. I also mentioned this on LinkedIn this week.
Prevention
In football, most teams try to strike a balance between their run game in the trenches and their passing game where the big gains can be made. Adversaries are nothing like that; balance doesn't work to their advantage at all, so they tend to have somewhat predictable trends. These days adversaries are working the social angle, so your prevention efforts should be focused on employee education (especially your helpdesk and IT talent), and ensuring you have strong defensive controls at your public edge and corporate perimeter. This is even more critical if you use cloud technologies, and leveraging a platform that can help you maintain visibility is critical to your success.
The outputs a platform generates require you to have in-house personnel. In my opinion, the prevention phase of security should not be outsourced if your risk profile includes public-facing data sources. You need people who can manage things like access control, phishing protection, access brokers, API security, etc.
The size of this team will depend not only on your risk profile but also your risk tolerance. Figuring out a probable loss expectancy on revenue can help make the case for prevention resources that can help take a proactive approach to your company's defensive strategy. Remember, requesting resources requires careful articulation of risk to people who will only understand the dollars and cents NOT the technical aspects of the risk, so you have to explain it that way. Invest in resources that can manage security platforms, have a curious nature, and are good at documentation.
In my last shop we had a controls management team that handled access control for money movement systems, security systems engineers focused on managing our security platforms, and vulnerability management specialists who tracked vulnerabilities, documented them in a risk register, and worked closely with IT to either implement mitigations or patch in a timely manner and in accordance with change control.
Change control is also part of a defensive strategy, however, this tends to live in IT. If you have change management as part of your security program, leveraging a strong change management discipline that incorporates relativistic risk rating will save you a ton of time in the endless cycle that is today's patch management process.
Next week we'll close out with offense!
###


Streamlining Security in a Product Shop


The ’53-Man’ Roster for Security (Part 3 of 3)

The ’53-Man’ Roster for Security (Part 2 of 3)


The ’53-Man’ Roster for Security (Part 1 of 3)


Dear Congress, We need a privacy law.