Welcome back! Football's second week did not disappoint—the Eagles won despite offensive struggles, the Bengals suffered a heartbreaking home loss, and the 49ers continued their dominant trajectory. Games were decided by defensive performance, making this an ideal moment to discuss building an effective defensive security team.
Defense Strategy Overview
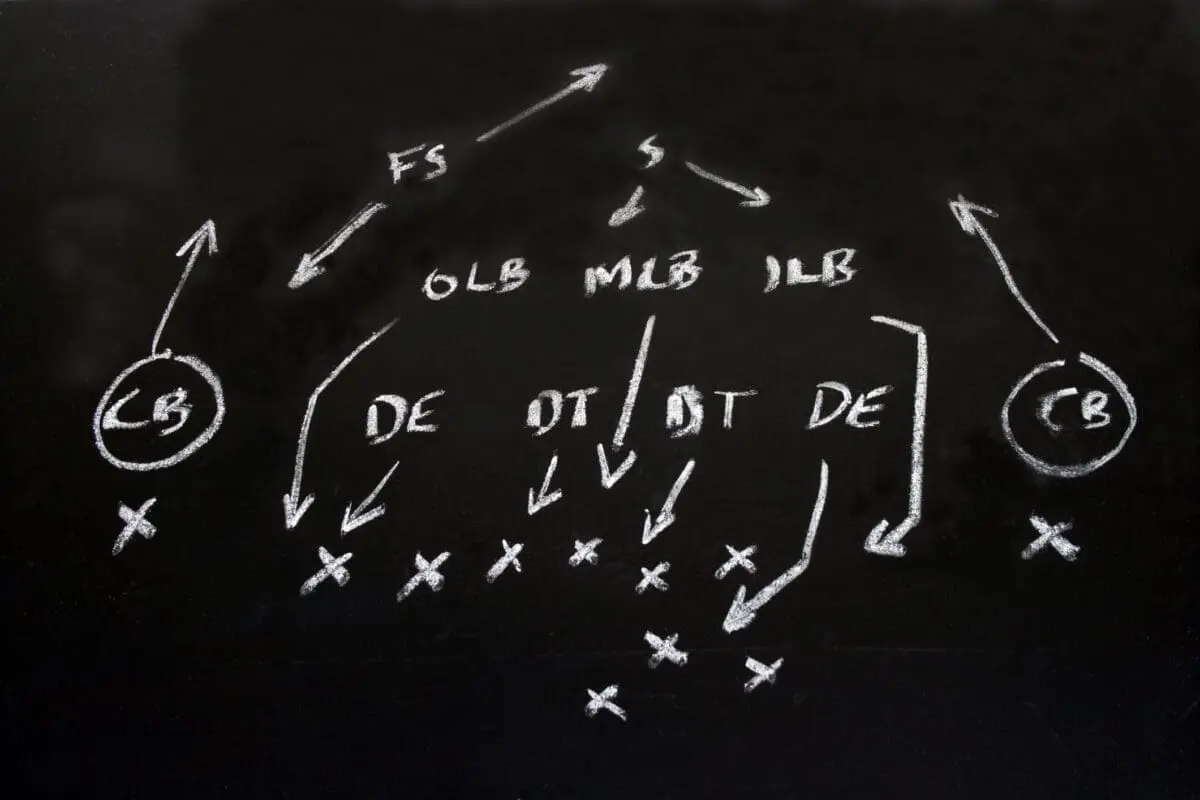
Football's defensive structure mirrors cybersecurity's Defense-In-Depth approach, consisting of three components: coverage (defensive backs), interior (linebackers), and line (defensive linemen). These correspond to security's prevention, response, and detection phases respectively.
Coverage/Prevention: Minimizes penetration attempts using a "bend don't break" philosophy. In security terms, this means making vertical movement through infrastructure impossible while identifying and containing lateral movement.
Interior/Response: Limits opposition movement and recognizes emerging problems before they escalate into incidents.
Line/Detection: The first defensive layer, preventing significant gains and frustrating attackers into critical errors.
Detection Phase
Detection can be outsourced but requires organizational oversight. DON'T RELY ON VENDORS ALONE! Internal resources should oversee vendor detection mechanisms and maintain consistent communication aligned with your security framework.
For in-house SOCs, establish clear roles: analysts examine tickets and correlate information, while engineers propose or implement tech stack changes following change control procedures.
Staffing depends on assessed operational risk. Many organizations use hybrid models—outsourced sunset-to-sunrise coverage with single-shift internal personnel during business hours.
Response Phase
Incident response may be outsourced, but organizations must maintain in-house management of response vendors. Critical elements include scenario testing and forensics, classification and analysis, incident response with validation, and containment procedures.
Two or three people working as a team can handle these responsibilities effectively. Response teams should validate SOC findings and develop playbooks—essential documents for both technical teams and business units.
Important Note: The MGM breach demonstrates the importance of developing strong playbooks, continuous testing, and routine tabletop exercises.
Prevention Phase
Prevention should not be outsourced if your organization handles public-facing data. This phase requires in-house personnel managing access control, phishing protection, API security, and related platforms.
Team composition depends on risk profile and tolerance. My previous organization included a controls management team (access control for money movement systems), security systems engineers (platform management), and vulnerability management specialists (tracking, documentation, remediation coordination).
Change control disciplines incorporating relativistic risk rating can significantly streamline patch management processes.
Next week, we'll conclude with Part 3, focusing on offensive security strategies.